
Growing tired of OneTrust? Migrate seamlessly with Ketch Switch

Most companies have no idea what data is actually being collected on their websites, and transferred to third parties—and that’s exactly the problem.
Data Sentry, our newest product at Ketch, exists for one reason: to give privacy and security teams real-time, actionable visibility into how data is collected, where it’s going, and whether it’s happening with consent.
Data Sentry is a new kind of tool. Not a checkbox. Not a banner. It’s a frontend data map—a continuous scan of live data collection behavior across all of your digital properties, tuned to the exact kinds of violations that lead to CIPA lawsuits, VPPA claims, and regulatory investigations.
Let’s break it down.
Most companies don’t fully understand the scope of data collection happening across their websites and digital properties. It’s usually not nefarious—it’s a challenge in visibility. Between third-party tools, dynamic scripts, and complex tag configurations, it’s easy for data to move in ways that no one on your team intended or approved.
This lack of insight creates real risk. Hundreds of privacy demand letters are sent every month, often focused on exactly these blind spots: tracking technologies that activate post-opt-out, session data quietly sent to analytics vendors, or consent signals that break down midstream.
Legacy tools haven’t kept up. Cookie scanners show what’s being stored, but not what’s being transmitted. Code scanners can help, but they miss what actually happens in the browser when a real user interacts with your site.
Data Sentry fills this gap. It’s a frontend data map that continuously monitors live network traffic from your site, capturing what’s being collected, where it’s going, and whether it aligns with your consent policies. It provides the same visibility that regulators and plaintiff’s attorneys already have—and that most companies urgently need.
Privacy enforcement is shifting—and fast. What used to be a legal gray area is now a well-lit target, especially for plaintiffs’ attorneys armed with old laws applied to modern tracking.
Two of the most commonly cited statutes in recent privacy litigation are the California Invasion of Privacy Act (CIPA) and the Video Privacy Protection Act (VPPA). These laws weren’t written with pixels and session replay tools in mind, but they’re now being used to challenge digital practices like:
Hundreds of demand letters are being issued every month, and plaintiffs’ firms are increasingly aggressive. (Keep reading: Wiretapping laws in the digital era: how to protect your brand.) But it’s not just the plaintiffs getting smarter—regulators are leveling up too.
The New York Attorney General’s office recently published technical guidance for website privacy controls, showing an increased focus on how data flows actually behave in practice—not just what a policy says on paper.
That means in-house privacy leaders need to stay sharp. The bar is rising. Regulatory investigations are getting more sophisticated. And the best defense isn’t reactive—it’s knowing, with certainty, how your site behaves under scrutiny. This is exactly why we built Data Sentry. To provide the kind of technical visibility that helps you catch and correct issues before they escalate into legal or regulatory action.
Data Sentry is about avoiding risk, and more—it’s about running a program that’s defensible, auditable, and built for how privacy is enforced today. Here are the three main capabilities we’ve built based on real customer pain and real enforcement patterns.
Data Sentry scans the actual network traffic generated by your website. That means every outbound data packet is analyzed to show you:

This is critical visibility. Most teams assume their privacy policies and CMP settings are being followed—but they rarely confirm it against the real data leaving the site. Data Sentry gives you proof, not assumptions.
You’ve got a consent banner. You’ve got “Do Not Sell” toggles. But what’s happening after a user opts out?
Data Sentry runs continuous checks to confirm whether data collection really stops when it’s supposed to. You’ll see:
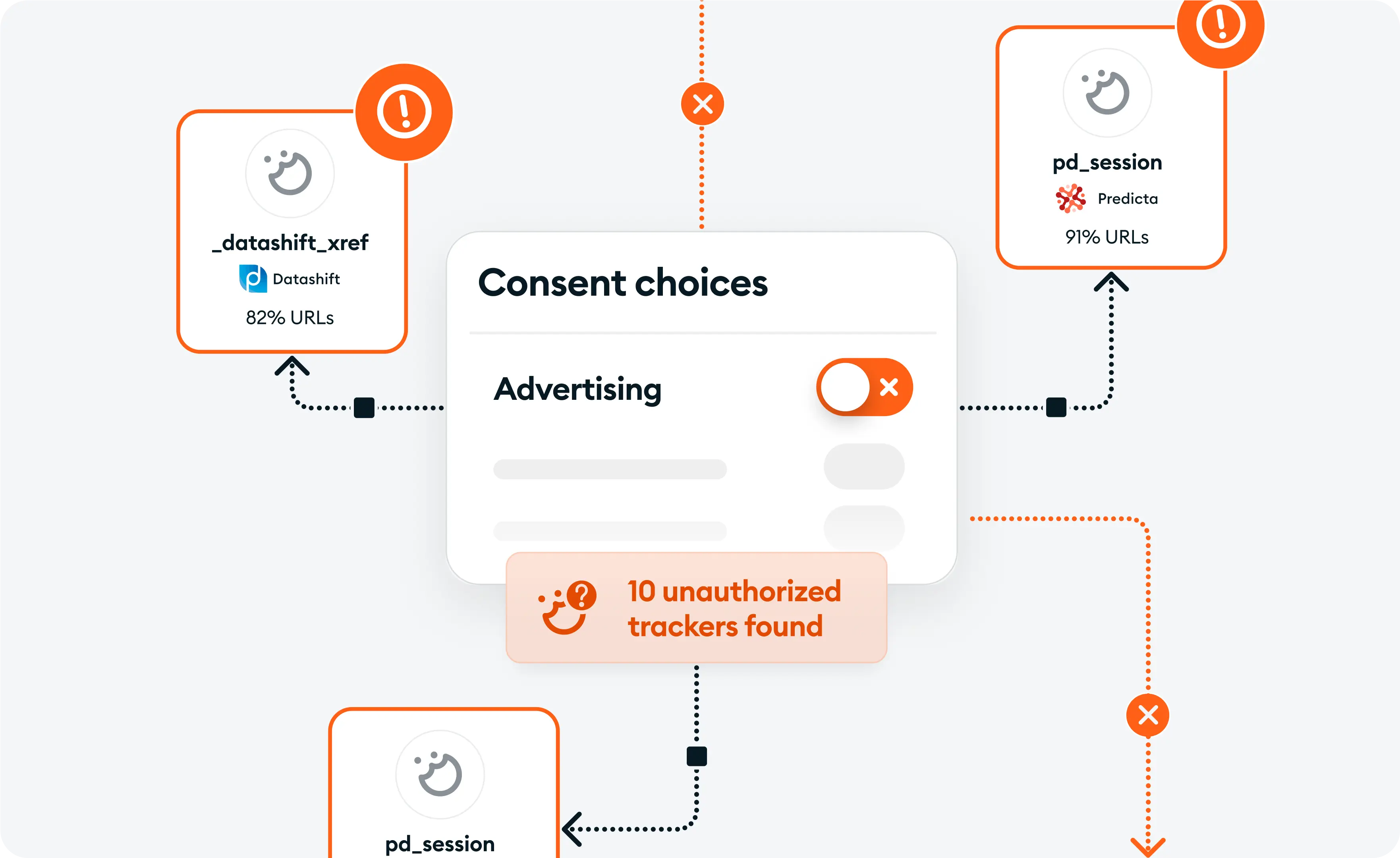
This capability directly reflects how regulators and attorneys evaluate your website. They click “opt out” and watch what still loads. If you’re still leaking data, you’re exposed—and now you can catch it before they do.
It’s not enough to just set consent preferences. You have to ensure those signals are passed and respected across your vendor stack.
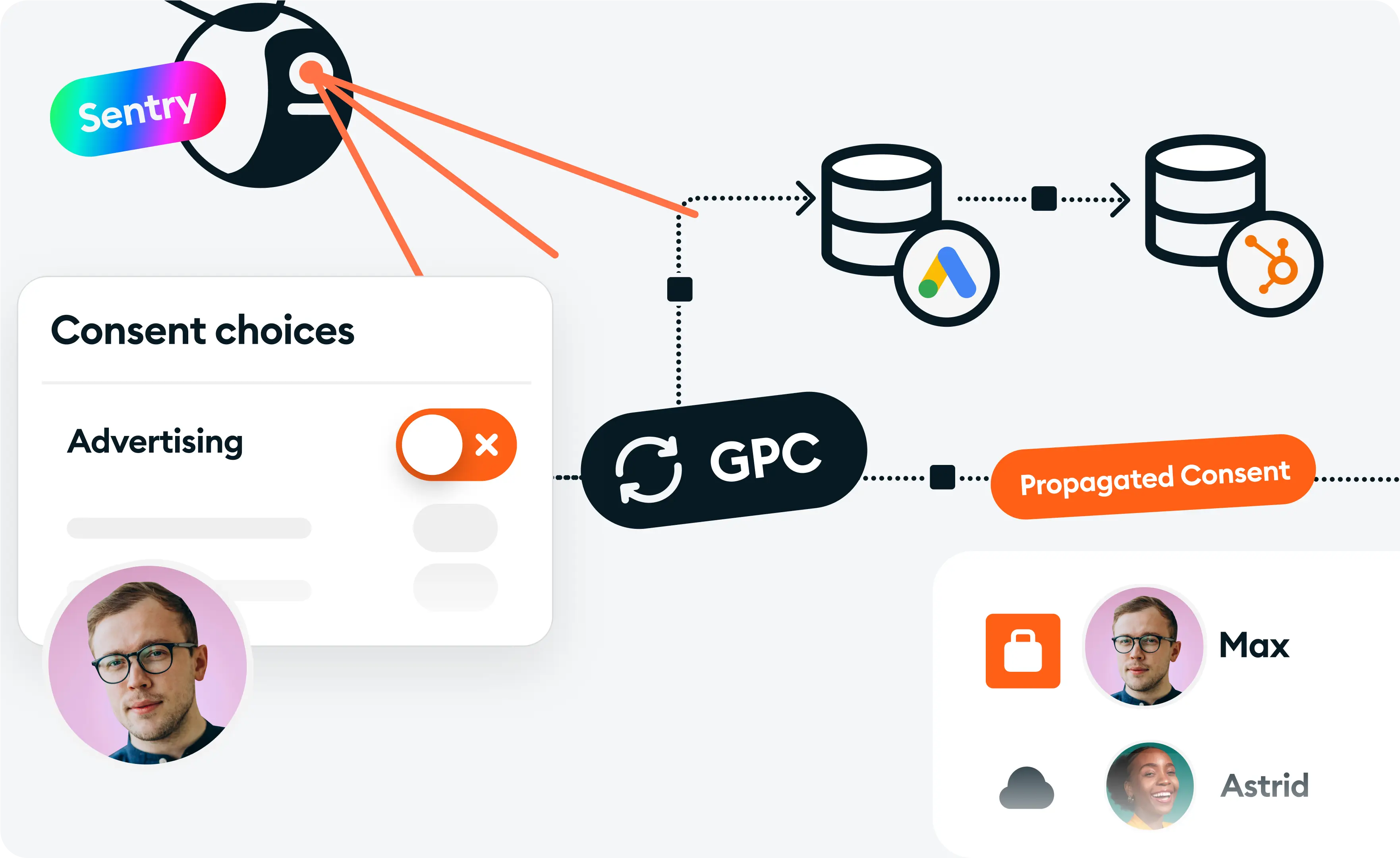
Data Sentry verifies signal passing across multiple industry frameworks, including:
You’ll get:
Think of it as consent enforcement QA: automated, continuous, and ruthlessly objective.
Most tools in this space are niche and limited at best, woefully inadequate at worst. Here’s what’s different about Data Sentry:
Great. You should! Data Sentry doesn’t replace your CMP—it validates that it’s doing its job.
Think of it like this: your CMP handles the consumer interaction (and depending on your set up, might even handle the passing of consent signals to systems and apps). But what do you have in place to validate that your CMP is performing correctly? That tags are accurately categorized, and stop firing after a consumer opts out?

You can’t control what privacy lawyers or regulators do next. But you can control how prepared you are.
Data Sentry is about getting proactive. It’s about knowing what’s happening on your site, in real time, and fixing issues before they escalate. Learn more, schedule a demo, and stop flying blind.
